iPhone Data Recovery
 Phone to Phone Transfer
Phone to Phone Transfer
The easy 1-Click phone to phone data transfer to move data between iOS/Android/WinPhone/Symbian
Restore-iPhone-Data Products Center

 Android Data Recovery
Android Data Recovery
The Easiest Android data recovery software to recover Android lost or deleted Files
 Phone Manager(TunesGo)
Phone Manager(TunesGo)
Best iOS/Android phone manager tool to manage your phone’s files in a comfortable place
 Phone to Phone Transfer
Phone to Phone Transfer
The easy 1-Click phone to phone data transfer to move data between iOS/Android/WinPhone/Symbian

iOS Toolkit
A full solution to recover, transfer, backup restore, erase data on iOS devices, as well as repair iOS system and unlock iPhone/iPad.

Android Toolkit
All-in-one Android Toolkit to recover, transfer, switch, backup restore, erase data on Android devices, as well as remove lock screen and root Android devices,especially Samsung phone.
Editor’s Note: These days we have a circle of friends must be the outbreak of the blackmail event on Friday scraper it In fact, the blackmail virus is not only recently discovered new varieties, hackers use extortion money can be traced back to more than a decade ago. So “old” software virus in the ever-changing technology today is still favored by hackers, and can cause great destructive power, what is the reason?

Learn More:
Recover Encrypted Data from Wannacry Virus Infected Computer
How to Repair Damaged Video File due to WannaCrypt Virus Attack
Hacker’s threshold is getting lower and lower, the future of network security in the end there is no guarantee?
With New Digital Tools, Even Nonexperts Can Wage Cyberattacks
Hackers are gradually found, and stolen data compared to kidnapping data can make more money.
On Friday, a network of more than ten years of history – blackmail software (ransomware) (http: t.cn/RaTj9Rr) again raging in the world. Cybercriminals use it to control hundreds of thousands of computers worldwide, the US logistics giant FedEx, the NHS, the Chinese universities, and even the powerful Federal Ministry of the Interior in Russia.
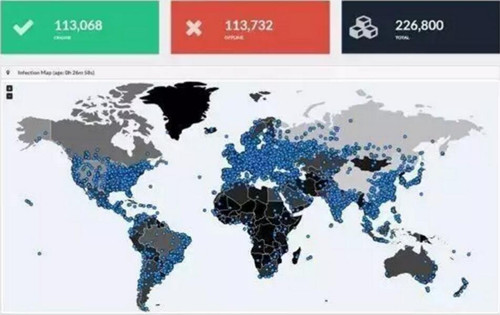
WannaCry Ransomware virus infection within 24h of the area
On Saturday, investigators have not yet found the scenes behind, and network security experts around the world are still trying to stop the spread of extortion virus. In Europe, carmaker Renault announced on Saturday that its French headquarters had been attacked by a blackmail virus, and that it was in a factory in Slovakia because of the fact that it had been seriously affected by many universities and institutions in Asia, The sudden “outbreak” has been closed.
At present, the US computer users by the less affected, this is because after the attack on Friday, a 22-year-old British information security researcher inadvertently find out the virus Hidden in the “delete switch”, successfully prevented the further spread of the blackmail virus.
In fact, the blackmail virus is nothing new. Over the years, companies or individuals have been attacked by the virus. Often, their computers are locked by the virus, and the only way to unlock is to pay a ransom for behind the scenes.
And cybercriminals are gradually found, with the Serbian virus to lock the victim’s computer in the important documents for extortion, is the shortest time the fastest way to make money. With high-strength encryption technology, difficult to track electronic money such as Bitcoin, and even some paid to help redemption of data after the site, these new tools can easily lock the victim’s data. That is, this form of cyber theft is becoming more and more simple.
“You do not even have any skills to” extort “someone else,” said Jason Rebholz, senior director of Crypsis Group, a computer security services firm. The company has helped dozens of victims of extortion.
With extortion software, even if not a computer expert, you can also become an Internet thief. Previously, hackers have a certain skill and creativity to cheat money. For example, the need to pay for the fake anti-virus software, claiming to be able to clean up the computer; sometimes, they will be installed in your computer Trojan program, once you online electronic transactions or enter the bank information, these malicious programs will steal credit card password; There are some outdated illegal intrusion is stolen a variety of personal certificates, resale sold to the dark network.
Four years ago, investigators found a variation of about 16 blackmail viruses, which were predominantly popular in Eastern Europe. And now there are dozens of extortion virus, and this hidden behind a perfect underground industry, but to seize the scenes behind the black hand is very difficult.
Relative to the previous small-scale attacks, the attack on Friday is a big outbreak of the virus. This time, hackers use a loophole in the Microsoft server, and this vulnerability was first discovered by the US National Security Agency (NSA), last month was a group of anonymous hackers leaked to the Internet (http: t.cn/RaTjRg5). This vulnerability makes the extortion virus can spread between the server, and locked all the files can be locked. More than 70,000 organizations in this event have become victims.
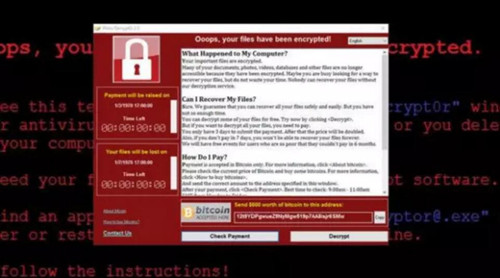
Computer infection after the interface of Wannacry Virus Ransomware Attack
According to data provided by Elliptic, a company that tracks online transactions (including virtual currency), several of the thunderbolt-related Bitcoin accounts have received a ransom worth $ 33,000 as of Saturday afternoon, and that number May increase.
This attack should not be so shocking. As the data gradually become the lifeline of people, cybercriminals extortion means more and more advanced, and the ransom is also more and more “lion big opening.” Five years ago, Eastern European hackers locked the victim’s computer, usually requiring only $ 100 to $ 400 ransom. At that time, there were not many people who paid off the criminals, because technical staff and security experts were able to find a way to unlock. In 2012, according to security experts estimate that only less than 3% of the victims paid a ransom.
And now, the proportion of payment of ransom has risen to 50%. And those who refuse to bow to the people, either their own enough backup, or psychological conflict, and some people can not afford a huge ransom.
The ransom is as low as one dollar (about $ 1,700), up to 30 bits (about $ 51,000), and the middle ransom has four more dollars (about $ 7,000), says Crypsis Group researchers. Compared to credit cards, remittances, Bitcoin more difficult to track, this way is simple and anonymous, so the network criminals are in the form of royalties to receive ransom.

Moscow city important city of Podolsk, because of last Friday’s hacker attacks, the city’s driving school can not issue a driver’s license
Moscow city important city of Podolsk, because of last Friday’s hacker attacks, the city’s driving school can not issue a driver’s license
There is even a saying called “extortion software as a service” – imitating the Silicon Valley famous “software as a service”.
Now anyone can download a blackmail software from the Internet, use it to lock someone else’s computer system, ask the other to pay ransom in exchange for documents. If the victim pays, then the provider of blackmail software can get a certain percentage of dividends.
Extortion software also provides customer service line, the victim to make a phone call, someone will tell them how to pay, and even online chat. “Some amateur extortion virus attackers may not recover the victim’s data after receiving a ransom, and professional hacker organizations will unlock the file in order to maintain their reputation and avoid” business “losses,” Rebholz said.
One of the notorious hackers is called Sam Sam, the rudder prescribed by the organization is the highest – 25 to 30 bits, but they receive the money and promises to unlock the file.
Most small and medium-sized companies will pay ransom as required because they generally do not have backup data, and no other options, Rebholz mentions. “In most cases, the data is the blood of the business, these companies either choose to pay good deal, or choose to give up business.”
Cybercriminals also aim at the university because the university usually needs to share a lot of information, so there are more open systems.
At the same time, they also found that the hospital is also a fear of “soft persimmon”. Friday’s blackmail virus attacked the British hospital computer system, triggering an unprecedented emergency. Hackers blocked the patient’s history, which makes the emergency room doctor helpless, had to “shut out the patient.” Imperial College Healthcare, located in London, suffered 19 extortion attacks over the past year.

On Friday the London hospital suffered Wannacry virus attack, the hospital emergency transfer of patients
FBI survey shows that from 2015 to 2016, the United States was disclosed the case of blackmail virus doubled, and hackers received ransom up to 1 billion US dollars.
In 2016, hospitals in California, Indiana, Kentucky, Maryland and Texas received attacks on extortion. Last February, a Los Angeles hospital paid $ 17,000 to hackers in order to unlock computer files.
In fact, on Tuesday, Dr. Krishna Chinthapalli published an article in the British Medical Journal (http://www.bmj.com/content/357/bmj.j2214), warning that there would be a hacker attack The He also cited a report, pointing out that one-third of the British National Health Service was attacked by a blackmail virus last year.
“In the past three months, health care workers have been preparing for possible attacks, who are ready for a bit of special currency and a professional accident copester,” said Chris Camacho, chief strategy officer at Flashpoint. “The New York company tracks Friday’s virus attack.
Nearly half of the blackmail virus attacks are done by inducing employees to click on messages, and sometimes criminals take a more complex approach. For example, a watering hole attack first infects a website with a blackmail, and when the user visits the site, the blackmail software is automatically downloaded to the user’s computer.
Rebholz said the other half was attacked by “violent” means. Hackers will first find an organization’s software vulnerabilities, low security passwords and other unencrypted electronic channels, and then block as many files as possible. According to Crypsis Group, Symantec and other companies, the SamSam organization is in this way, each year blocked hundreds of thousands of computer systems, in order to earn the industry’s highest bitmember ransom.
It seems that no one can immunize the extortion virus. In January, hackers “kidnapped” data from a small cancer specialist in Indiana, controlled the agency’s main server and standby server, and raised 50 rupees (more than $ 87,000) in ransom. However, this charity refuses to pay.
And the terrible thing is that some attackers even in the “love” in the name of the implementation of extortion. Rebholz recently traced to a blackmail attack, the attacker tried to persuade the victims, their donated “love” will be used to fund the sick children around the world.
“This is what we are doing now, and these” actors “are posing as charities, deceiving people’s feelings and trying to cast a beautiful veil on their criminal activities,” Rebholz exclaimed.
Tips:Once your comptuer suffer a Wannacrypt Ransomware Virus Attack,the fist thing you need to do is against WannaCrypt.We will provides you some effective methods to against WannaCrypt ransomware virus attack,remove the wannacrypt ransomware,recover your encrypted files from WannaCrypt ransomware and repair damaged video file due to WannaCrypt virus Attack.Please keep reading as below tutorials.
Read More:
How to Recover Lost Data from a Virus Attack Computer
Recover Encrypted Files from Wannacry Virus Infected Memory Card and USB Drive
How to Recover Lost Data from iPhone iPad
How to Recover Lost Files from Android
How to Recover Phots and Videos from Broken Samsung
comments powered by Disqus